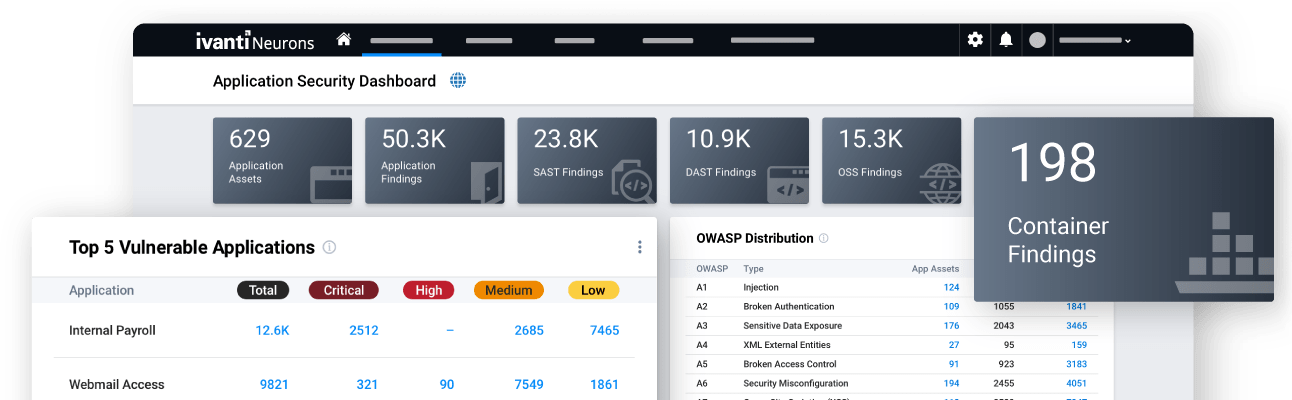
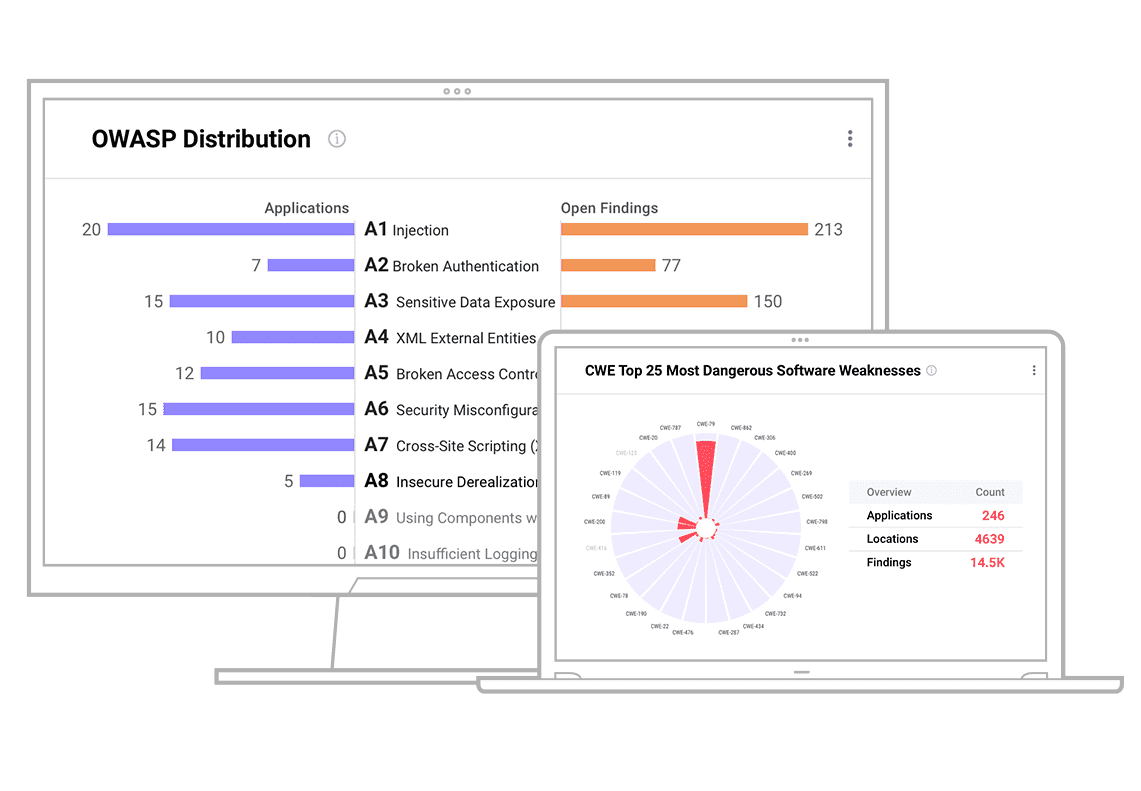
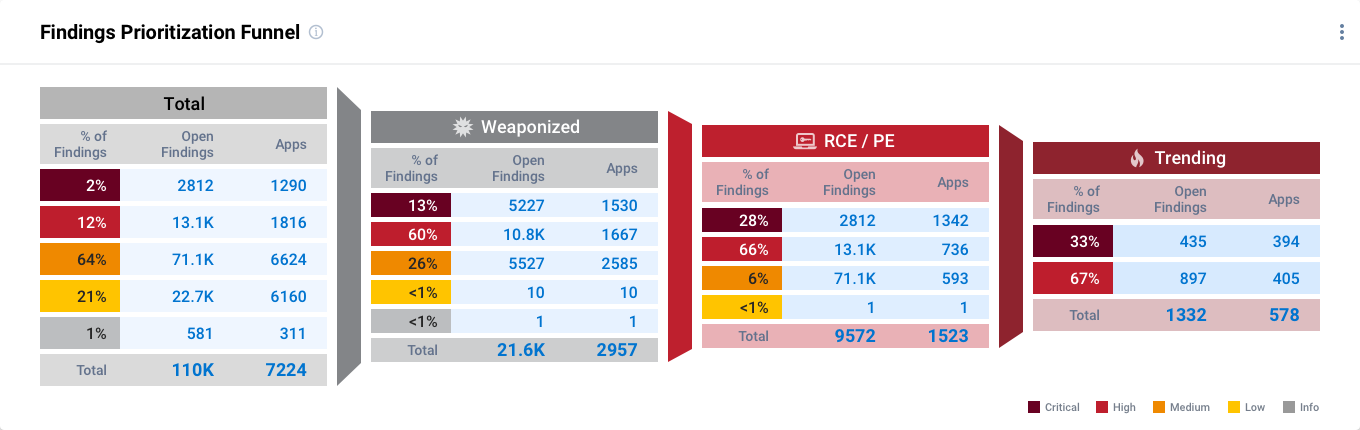
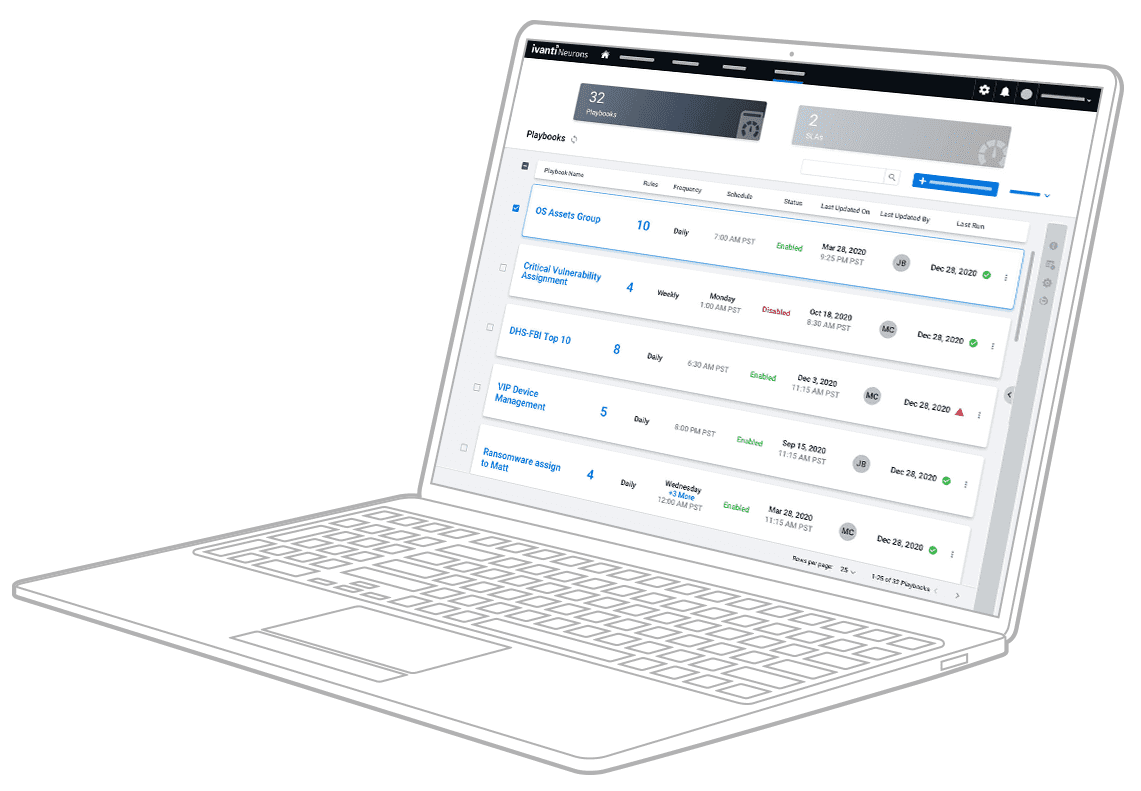
Make fast, informed decisions on where to direct development to fix vulnerabilities and weaknesses to improve the security of internal and customer-facing applications.
Diverse data sources
Capture a broad view of your cyber risk with data collected from application scanners (SAST, DAST, OSS, container), vulnerability findings from 100+ sources, and more.