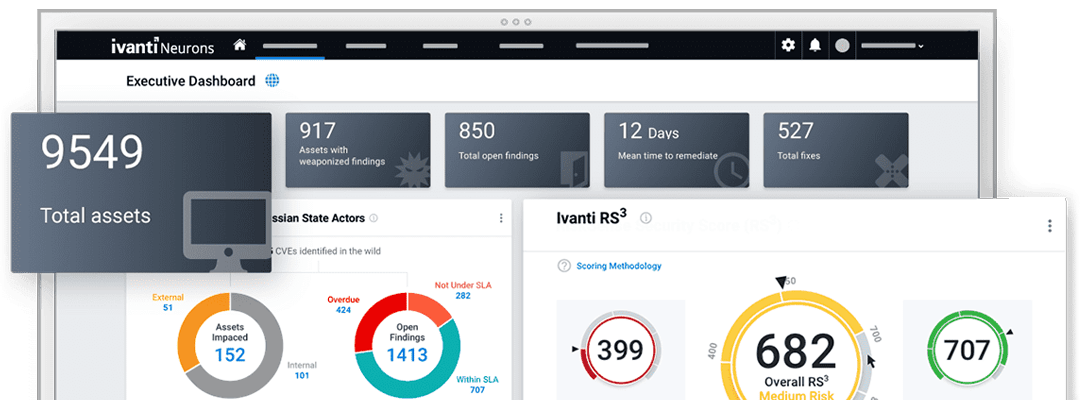
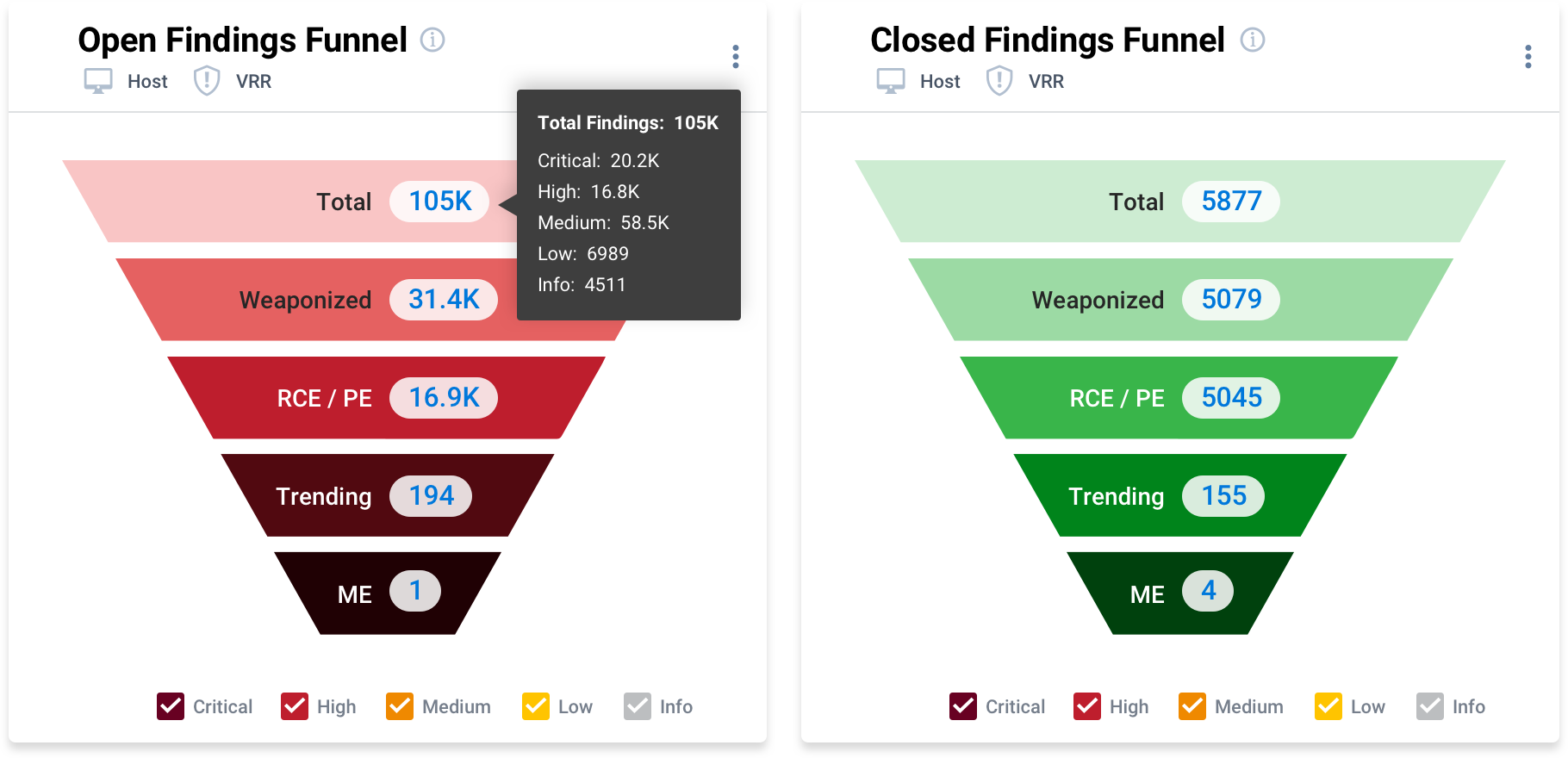
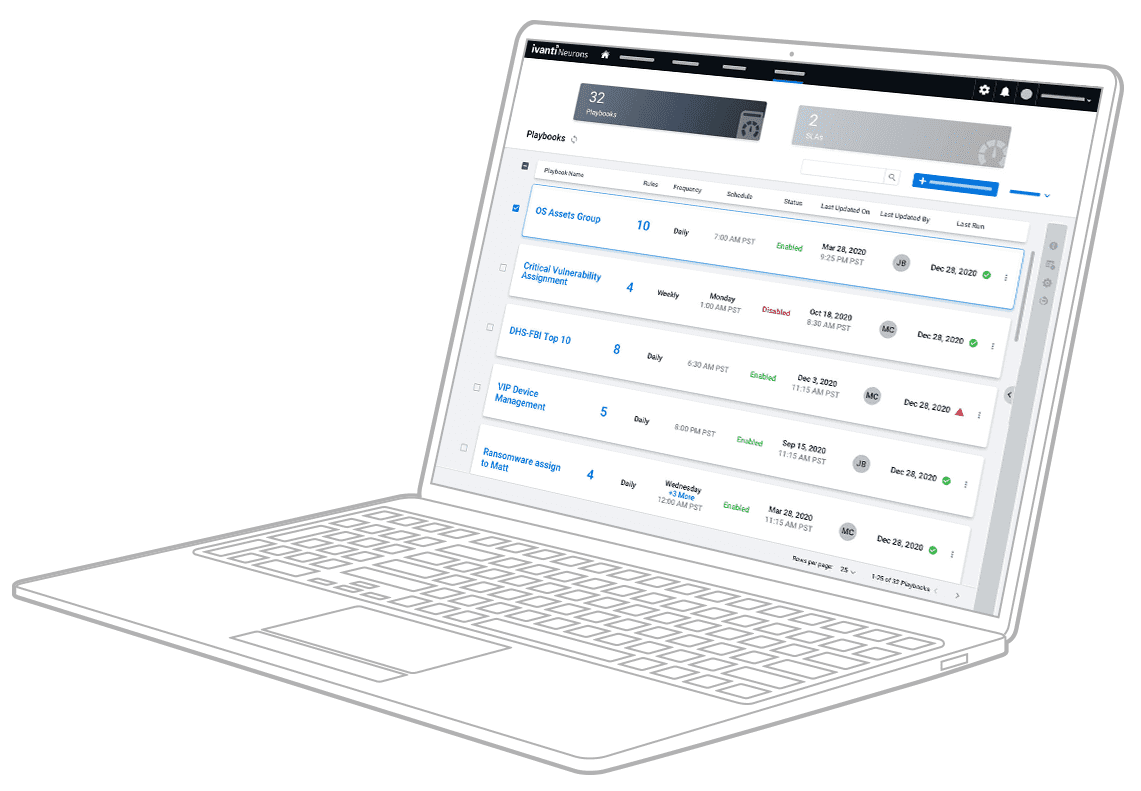
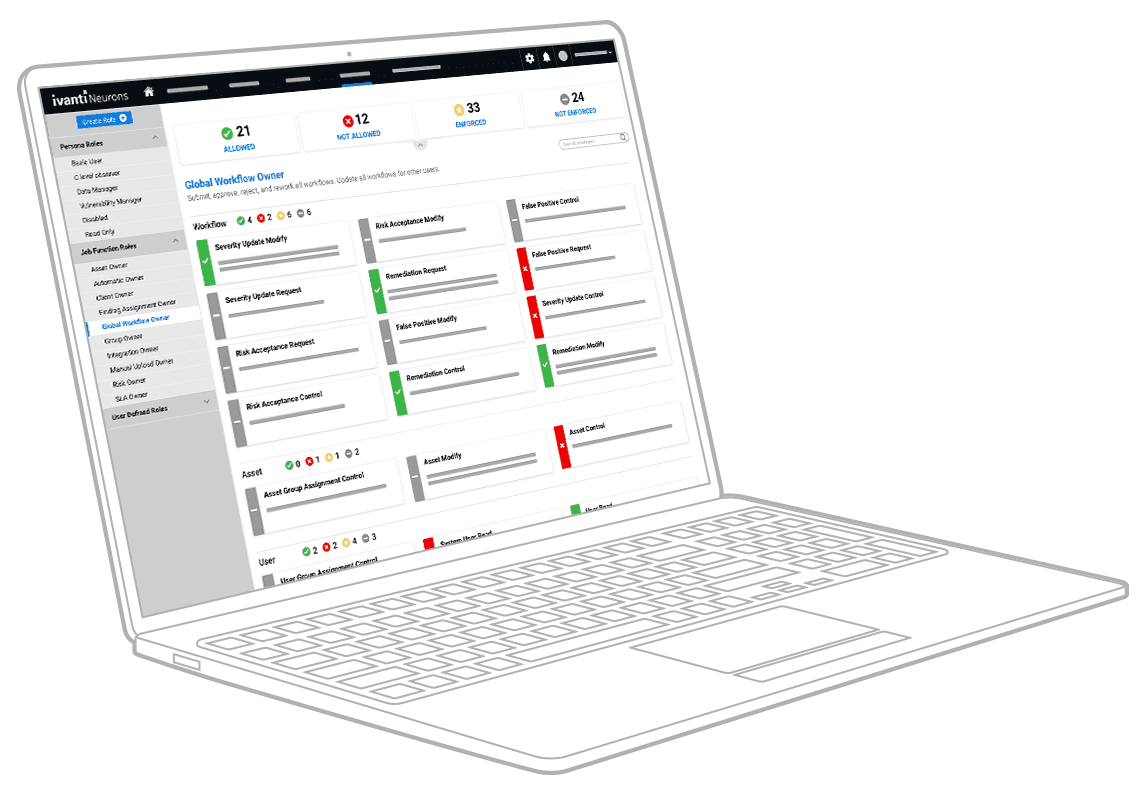
Measure and control your true cybersecurity risk with a risk-based approach to vulnerability management.
Diverse data sources
Achieve a wide view of cyber risk with data ingested from network scanners, vulnerability findings from 100+ sources, manual findings from research and pen testing teams, and more.