The Art and Science of Predicting Weaponization
*This post originally appeared on the RiskSense blog prior to the acquisition in August 2021, when RiskSense became part of Ivanti.
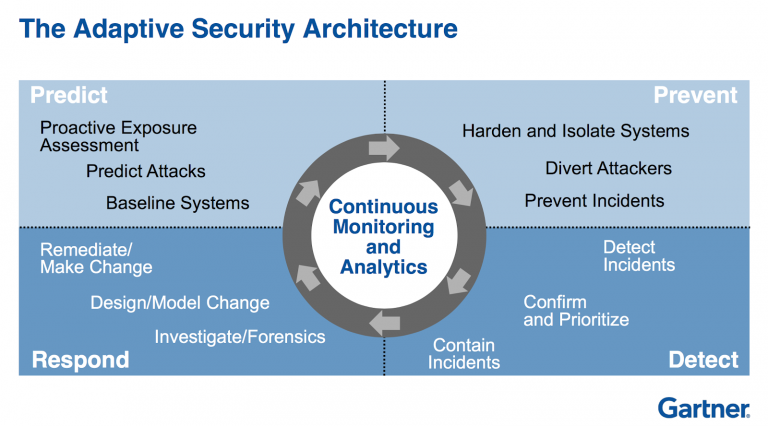
As threats have become more sophisticated and have increasingly turned to more adaptive and continuous approaches to security such as Gartner’s Adaptive Security Architecture. This model breaks security into the high-level categories of Prevent, Detect, Respond, and Predict. This last category of attack prediction has been one of the long-standing challenges of information security. Most security teams are overwhelmed with the volume of live threats, and anticipating what attackers will do in the future can seem almost impossible.
However, that is starting to change. The combination of new analytical models and real-world threat intelligence is enabling security practitioners to accurately predict and prioritize the vulnerabilities that attackers will target even before they are used in the wild. This allows forward-looking security teams to take a far more proactive approach to security that doesn’t wait on the attacker to punch first.
Weaponization is the Key
As most IT and security personnel can attest, the volume of vulnerabilities has exploded in recent years. While organizations have been overwhelmed with vulnerabilities for years, the problem has gotten much worse. A quick check of the National Vulnerability Database (NVD) shows that in 2017 the number of vulnerabilities essentially doubled as compared to previous years. In 2018 the number continued to grow, and thus far 2019 is continuing the upward trend.
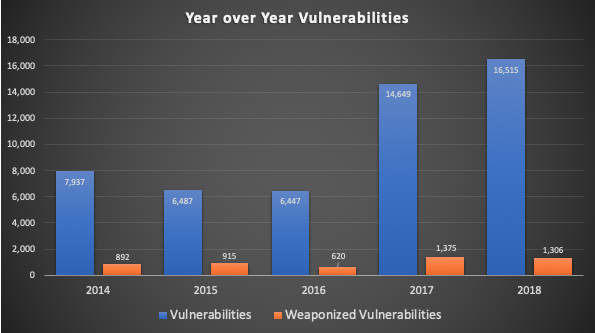
Patching each and every instance of every vulnerability is simply not possible for most organizations. However, all vulnerabilities are obviously not equal. The truly important vulnerabilities are the ones that have weaponized in the form of exploits or malware that can actually take advantage of the weakness. And as the chart shows, weaponized vulnerabilities are actually in the minority with less than 8% of vulnerabilities in 2018 being weaponized.
By focusing on weaponized vulnerabilities, particularly the ones that are the most popular in the wild, organizations can turn a virtually impossible task into one that is manageable. However, things get even better when we can start predicting which vulnerabilities will be weaponized even before the attackers start using them. Let’s take a look at how this sort of predictive capability works.
Building the Predictive Engine
To build a reliable prediction engine we need to combine multiple perspectives and types of intelligence. At the highest levels this will include AI and machine learning models to help reveal important traits of a vulnerability that are predictive of weaponization. However, we can also pair these analytical models with real-world intelligence gathered from hacking communities and the threat landscape. By combining machine and human intelligence we can achieve results that neither can do on their own.
Let’s first take a closer look at how we can design predictive analytical models. Conceptually, we want to look at vulnerabilities that have been weaponized in the past and find the hidden traits (or combination of traits) that they share in common. Machine learning can help us to identify the traits that most strongly predict for weaponization, and we can continually train and enhance the model over time based on real-world results.
For example, most organizations are very familiar with CVSS risk scores for a vulnerability. But by pulling apart and analyzing the base metrics underly a CVSS score, we can find traits that are much better predictors of weaponization than overall CVSS score. For example, finding vulnerabilities that have low attack complexity and include a remote-code execution or privilege escalation capability can be a good starting point.
We can then correlate that across other types of data such as CWE information that looks at the underlying weakness of a vulnerability. For example, the ability to run unauthorized code and bypassing protection mechanisms are strong predictors of weaponization. Next we can look at CPE or the type of vendor or asset that is affected. Attackers often have skills attacking particular common vendors. Also high-value Internet-facing assets such as the recent Apache Struts vulnerabilities can make very strong targets for weaponization. These are just a few examples, but it shows how we can train models to analyze readily available data sources to get new insights into weaponization.
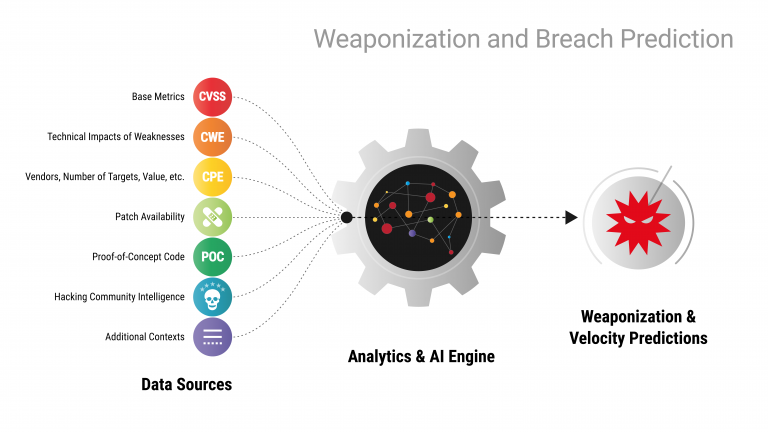
Likewise, our analysis needs to include a variety of real-world contexts. The presence of proof-of-concept code can strongly accelerate the speed of weaponization. Ironically, even the presence of a patch can play a role here, as attackers will analyze a patch to understand how to exploit a vulnerability. Of course, we also need to make use of intelligence derived from the hacking community itself. By monitoring underground forums where new threats are discussed, bought, and sold, we can get some insight into what threats are on the horizon.
Once again, these are just some of the many contexts that we can leverage for building predictive analytics. We can add or remove additional contexts as necessary. However, the real value is in the operational results. Instead of sorting through thousands of high or critical vulnerabilities, organizations can instead focus on the areas where the real attacks will target. And with predictive models, we can anticipate and prepare our defenses even before the threat exists in the wild.
